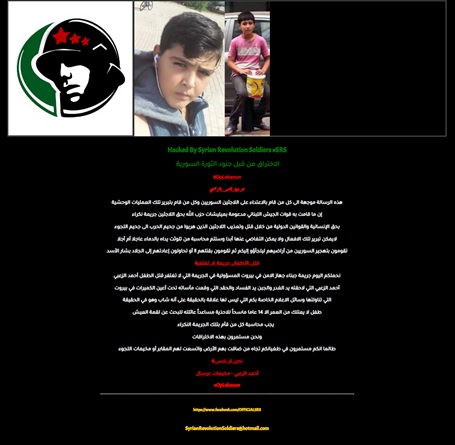
On Tuesday, many people noticed the official website of Rafic Hariri Airport had a different landing page. A group calling themselves the Syrian Revolution Soldiers (SRS) defaced the main page of the website to display a political message.
Recently, Lebanon has witnessed a slew of these attacks, with many of them targeting Lebanese government websites. In most cases, these groups have changed the display of the website’s homepage to deliver political messages. Why are these attacks occurring so frequently? Either the Lebanese government is not devoting enough resources to securing its website, or it does not have the technical know how.
Here is a list of the recently defaced Lebanese government websites:
SRS
| saida.gov.lb | 28/1/2019 | SRS |
| www.beirutairport.gov.lb | 28/1/2019 | SRS |
Chinafans
| fanar.gov.lb/o.htm | 2018/09/24 | ChinaFans |
| www.jbs.gov.lb/o.htm | 2018/09/23 | ChinaFans |
What is Web Defacement?
Like its name indicated, web defacement occurs when a hacker or group changes the face of a website and the message it delivers. Usually, hackers try to change the “face” of a popular website, generally to send political message, to emphasize that the owner of the website does not take the necessary security precautions, or to gain online exposure and recognition.
In order to successfully carry out a web defacement attack, a hacker breaks into a server, exploiting its security issues and vulnerabilities, and replaces the main website file (usually an index.php, index.jsp, or index.html) with one made by the hacker. To change the face, the hacker might publicly upload a file on the contact form on a website, which often do not have any filtering. Therefore, the hacker is able to load custom code to the server, which can tamper with the files.
In more other situations, hackers may use more complex techniques like phishing, code injection, XSS (Cross Site Scripting used in phishing attacks where a specially crafted URL request enables malicious parties gain important information about their target) , or Remote File Inclusion (RFI), which occurs when hackers upload a unique script to modify the server. Common targets are usually corporate and governmental websites.
The Lebanese government has consistently been a target of such attacks and most of the altered messages are political.
Web site defacement consist of key elements:
- A vulnerable system that can be exploited allowing unauthorized access by malicious party
- Existing web pages are modified or replaced with new text and graphics
- A motive behind the defacement (Malware spreading, political messages, hacktivism etc.)
Why are the Lebanese government websites so poorly protected? Usually, governments will put out a tender for technological companies to develop the website to fit the requirements and the needs of the government. This relationship is inherently problematic because governments often disregard good information technology practices are disregarded and many companies do not offer strong customer support once they have completed the contract. Constant updates are complicated and costly.
Such policy practices lead to poor design of web applications, which makes them vulnerable. Most websites are based on PHP/ASP or a Content Management Software, like WordPress. The government should constantly monitored and updated because every day there are new exploit..
Recommended counter-measures
- Use the latest version of whatever Web server a web application is hosted on, Database server, FTP, hypertext process and shared hosts should be avoided unless their IT service is of high maintenance.
- Apply appropriate updates/patches on the OS and Application software when available.
- Every entity buying a software, should hire penetration tester to assess and audit the complete security of a web application, web server, database server periodically (It’s continuous maintenance and updates, it’s not a one time thing) and after every major configuration change and vulnerabilities found
- Security Information and Event Management are a crucial requirement (SIEM) and possibly DAM (Database Activity monitoring)
- Removing the defaced webpage isn’t enough, the targeted web app should be searched and analysed to find where they got access from. Sometimes a webshell might persist on the web server silently without being removed, so even after a patch, malicious parties always have access as their evasion strategy is still active.
- Periodically update password for accounts, making them complicated and difficult to brute-force (a form of attack allowing the attempt of many possible passwords unless one username password combination works)
(Photo from Pexels.com)
——————————————————————————————————————–
Ragheb Ghandour is a PhD Student. He is a computer scientist with a Masters degree in Information Systems for Risk Management and a cybersecurity enthusiast. He mainly focuses on human-error in cybersecurity and the rights to online free expression and privacy.