Happy Data Privacy Day!
More than half of the world is now online. Companies are collecting, leveraging, and monetizing our data, often exposing it to third parties. We continue to call on governments in the region to respect our privacy and set legal frameworks to protect privacy and personal data, and corporations to stop siphoning our data and sharing it with governments and third parties. However, protecting your privacy is also your responsibility because there is always something to hide.
On Data Privacy Day, the international holiday promoting privacy and data protection best practices, we are sharing a list of recommendations on how to protect your privacy online.
Decrease the amount of data apps collect about you.
Check the permissions the app requests. (Image via Stockvault)
When you install an app, it will request access to your device’s data and capabilities including its location, storage, contact list, and microphone access. In 2017, a study found out that thousands of apps were leaking sensitive personal information to other apps, which users had not granted access to. In addition, Google third party apps can read your and analyze your emails. What do you do in this case?
- For apps downloaded from the store, check the permissions the app requests before you install it. You can do so on the app store.
- Deny unnecessary access by changing the permissions of an installed app on an Android Device.
- As for Google third party apps, go to myaccount.google.com, under Sign-in & Security, click on “Apps with account Access” Click on “Manage Apps”, “Manage Apps”, then on any “Third-Party” apps, and finally, “Remove” its Access.
Spyware campaigns are in the rise. Take precautions.

The pages phishing links redirect you to often request personal information. (Image via Stockvault)
In the latest spyware campaign targeting MENA region countries, including Lebanon, the hackers circulated links with fake job listings, which contained word documents with fake job descriptions. When targets downloaded these documents, they ran malicious code. Here are a few tips for detecting phishing links:
- Phishing links are usually malformed hi. For example you might see http://googl[.]com instead of http://google[.]com.
- Hover the mouse over the link, which might reveal either an IP address or a web address, usually in a little yellow or white box.
- Check the “From” and “To” fields of the email. If the email is not addressed to your email directly, something is “phishy.”
- Complex domain names with many dashes, numbers, and dots are likely fake links.
- The vast majority of big companies have adopted https. If you do not see a lock on your browser URL field, don’t proceed.
- The pages that phishing links redirect you to often request personal information.
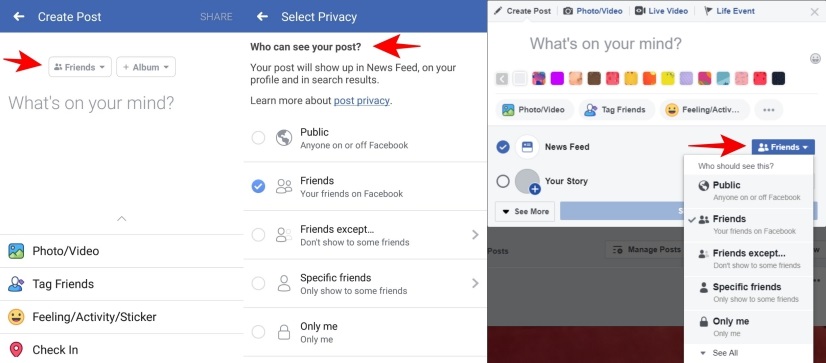
Protect your Facebook posts’ privacy.
Until recently, posts on Facebook were public by default, so they can be either seen by your friends, friends of friends, or the general public. The privacy of you Facebook posts is crucial if you want to control the reach of your posts and conceal them from people you do not know.
- On your desktop, go into your settings, click on “Privacy”, then to “Your Activity” tab. Click on Edit and choose your intended audience (Public, Friends, Friends except…), or you can change the privacy of the post simply by clicking on the button next to “News Feed”.
- On your phone, you can control the privacy settings of each post by clicking under your name on the Facebook app when writing a post.
How to recognize fake accounts that are mostly used by attackers.
A fake account is not openly tied to any real identity. It can be just a bot to create likes and follows. For example, governments and police forces may use fake accounts as a honey pot to target activists. Fake accounts are also used to hack into your profile and steal your identity and personal information, such as your banking details. How can you avoid them?:
- Do not accept a friend request from someone you do not know, even if you have friends in common. A fake account might have added some of your friends already.
- Check for inconsistencies or contradictions in the profile; fake profiles might have unusual biographical information, empty profiles, or an unnatural number of likes.
- Block the account because even if you do not accept their friend request, it could still follow you and see your posts.
- If you did accept a friend request from someone you do not know, never click on a link sent by them. This might lead you to download malware, which could infect your devices.
Data Privacy Day is a good reminder to protect our personal data and information and demand that corporations and governments to stop exploiting it and treating it as a commodity