On Monday, Lebanese daily Al-Akhbar revealed that touch, one of the two mobile operators in Lebanon, is considering purchasing DPI (Deep Packet Inspection) technology from Nexius, a U.S-based communications and software company. The newspaper also reported that Alfa, the other mobile operator in Lebanon, paid $3 million for the same technology a year ago, but still has not received it. In our own research, we found an expired Beirut-based Nexius job posting from March 2018, recruiting DPI “experts.”
The telecom companies’ decision to integrate DPI has major implications on users’ privacy and could lead to an increase in targeted surveillance, both by state agencies and third parties.
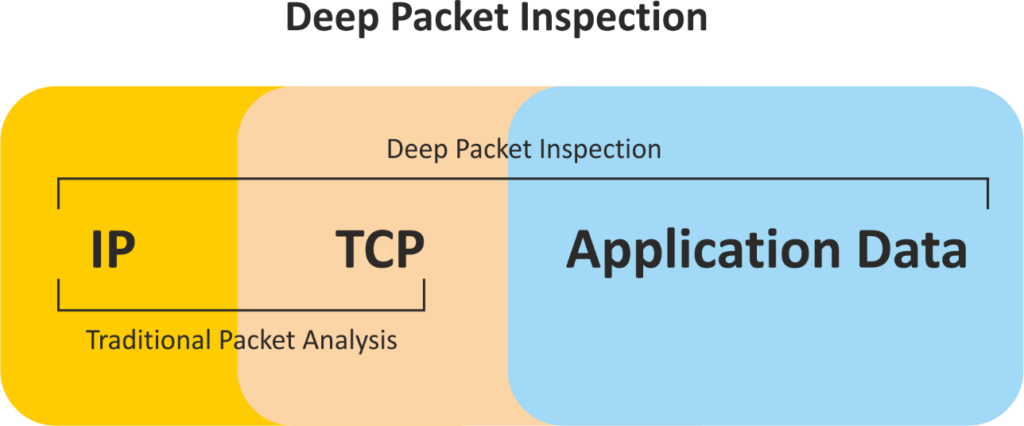
What is Deep Packet Inspection (DPI)?
When a user communicates with the internet, they are constantly sending packets containing relevant information. Internet Service Providers (ISPs) are then able to intercept the Network Communication protocols (TCP/IP, ATM, IPSec etc.) and detect whether a user is trying to reach a web browser, email, or other type of communication service. DPI technology can examine the data in the packet for unwanted online activity, such as spam, viruses, and intrusion, help the network filter content, and find statistical data about the complete packet structure.
Yet, DPI technology also gives the ISP a plethora of information about a user’s connection and usage habits, which can allow the operator to conduct behavioral analysis. DPI technology can read and analyze unencrypted messages and can automatically detect specific words. For example, if Alice sends Bob an email containing the words “I am gonna kill her,” the DPI operator might mark Alice as a potential threat and provide this information to government entities, even if it is clear Alice’s message is not literal.
Even when users are visiting HTTPS-encrypted websites, DPI can obtain information that violates their right to privacy. The user is still making Domain Name Server (DNS) requests, sent primarily through User Datagram Protocol (UDP); therefore, DPI technology will still collect any unencrypted links or unencrypted cookies sent without HTTPS. Moreover, DPI technology can also alter DNS requests and redirect users to different pages.
Why is DPI Technology Dangerous?
DPI technology enables massive data collection, which can facilitate mass surveillance. For example, data scientists can use it to track a person’s internet usage and determine behavioral patterns. By matching a user’s online behavior on their home network (DSL or other) with their 4G internet usage behavior, the operators of the DPI technology will be able to identify a user’s habits, frequently visited locations, and other sensitive patterns. This data raises concerns, as the ISP might sell the data to third parties or simply give it to government agencies. People have a reasonable expectation that their communications are private and collecting this data violates that expectation.
If the government, which owns touch and Alfa, does not enforce regulations to ensure the DPI technology respects users’ privacy, government agencies could conduct cyber-espionage operations, which is particularly worrying because the Lebanese Ministry of Telecommunications does not have the strongest cybersecurity track record.
The government would be able to monitor activists’ and journalists’ behavior at home and on connected mobile devices. From the number of bank transactions, to the most visited online applications, the operators of the DPI technology, in this case Alfa and touch, would have access to this information and be able to use it against users.
Recommendations
Below are a few privacy recommendations for activists, journalists, and other concerned citizens:
- Use HTTPS when browsing the internet. HTTPS can prevent ISPs with DPI technology from reading the application data content. Installing HTTPS-Everywhere on browsers is essential in this case, and avoiding plain HTTP links is highly recommended. Nonetheless, the ISP will be able to read metadata and collect fingerprints. For example, it would know if someone was using encryption, which might raise suspicion.
- Additionally, avoid phishing links, if the ISP is able to install Secure Sockets Layer (SSL) Interception technology on your device, it would allow the DPI operator to decrypt SSL, a standard security protocol, and read encrypted messages.
- A Virtual Private Network (VPN) can also protect users from ISP’s DPI because VPNs create a tunnel between the user and the VPN server. Therefore, all the data is encrypted through the tunnel. Still, the ISP would know the VPN’s IP address while it establishes the tunnel connection, thus disclosing the use of VPN and the actual server you are accessing.
Conclusion
Installing DPI will further impinge on the right to privacy in Lebanon because the phone companies, and in turn the government, will have access to more of the information citizens and residents are are transmitting. Last year, Citizen Lab reported that Turkey used DPI middleboxes, developed by American company SandVine, to redirect users “attempting to download legitimate programs to versions of those programs bundled with spyware.” Given the Lebanese state’s history of surveillance, and weak legal framework for personal data, security agencies could use similar tactics to target journalists, activists, and regular citizens.
Ragheb Ghandour is a PhD Student. He is a computer scientist with a Masters degree in Information Systems for Risk Management and a cybersecurity enthusiast. He mainly focuses on human-error in cybersecurity and the rights to online free expression and privacy.