Update— IMPACT responded to our concerns by suspending Grabajab’s access to patients’ data pending the resolution of security issues. Nonetheless, we are yet to learn the kind of data accessed by GrabAJab and how it was used and processed.
Grabajab.com, a vaccination platform launched by the Lebanese Ministry of Public Health (MoPH), was reported to be down for a few hours today, July 9, 2021.
The newly-launched platform, GrabAJab, was launched by the MoPH as “[a]n additional tool to help eligible individuals find earlier appointments in the vaccination sites.” It came after a series of vaccination and curfew-permissions platforms launched by IMPACT, an e-government platform initiated by the General Inspection in Lebanon. It was launched in June for booking appointments during vaccination marathons.
SMEX ran a surface security audit on Grabajab.com and found some serious vulnerabilities. Based on our findings, we recommend not using the platform before MoPH makes the necessary amendments to ensure your data is fully protected.
These are some of the technical vulnerabilities we found on the website:
- Application Programming Interface (API) access is available publically without Cross-Origin protections. The webpage listing the methods used by the platform to collect data and/or functions is not well protected and is easily accessible without the need for authorization.
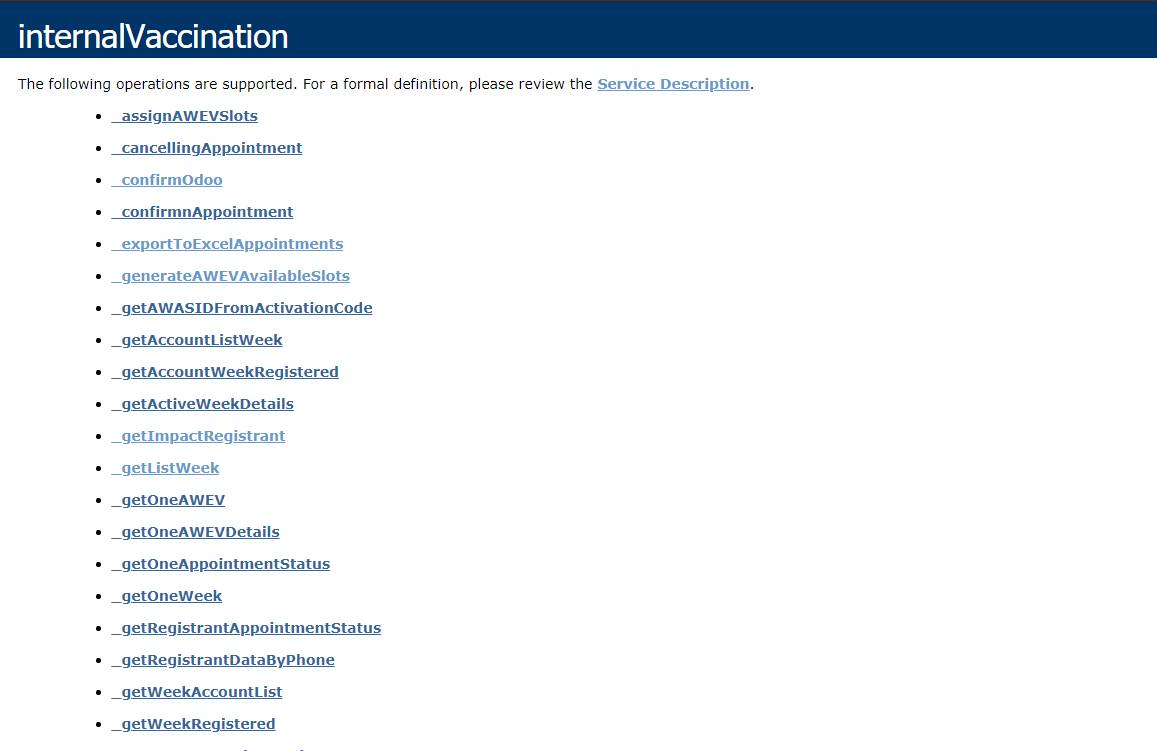
- The platform methods for reservations and registration are based on phone numbers and MOPHCOVAX ID which are publicly available for access without boundary protection. A malicious entity can abuse the platform using brute-force (a hacking method) available to obtain access or abuse the platform.
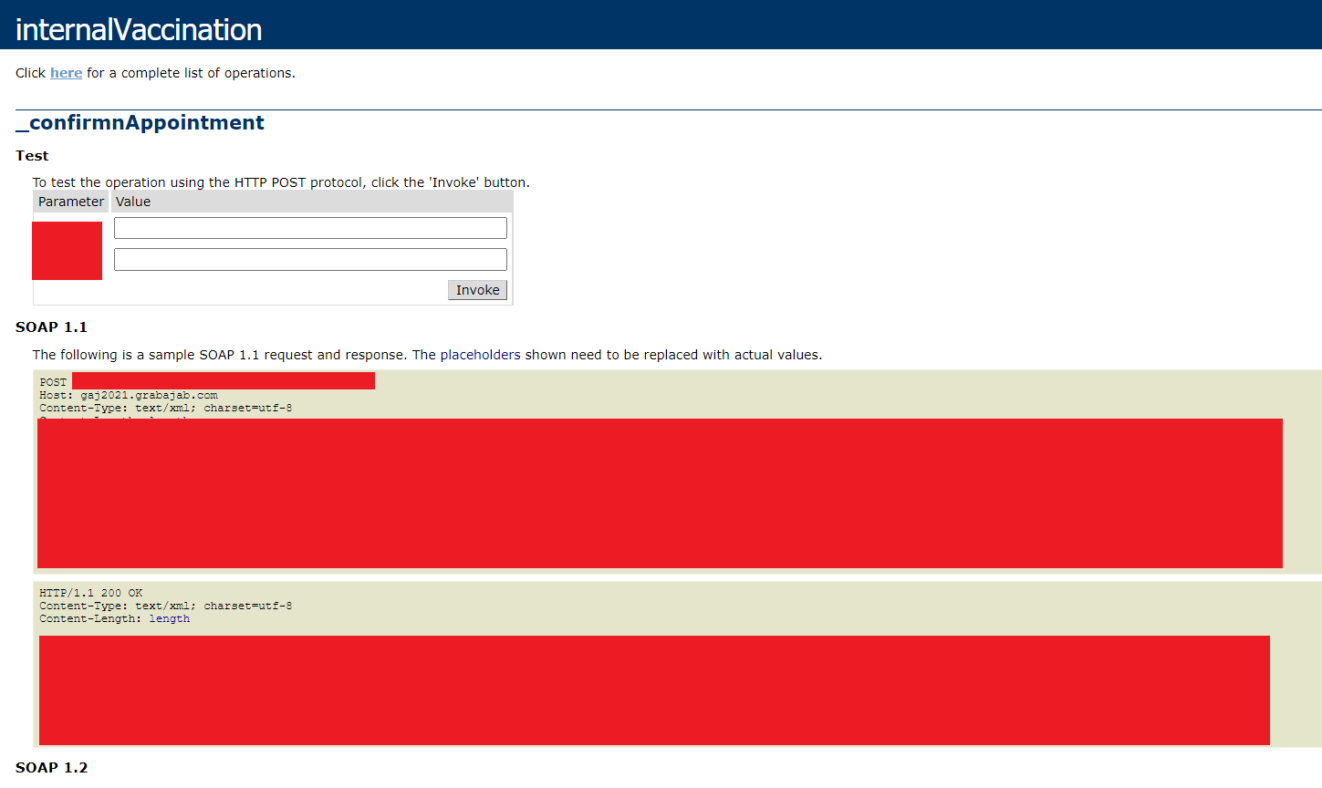
- Simple Object Access Protocol (SOAP) 1.1 and SOAP 1.2 parameterization is accessible publicly. SOAP is a messaging protocol specification for exchanging structured information between web services in computer networks, which indicates that other platforms are using Grabajab, probably for reasons related to the vaccination campaign.
- No Secure Sockets Layer (SSL) was detected. SSL is a cryptographic protocol that secures communications between the device, website, network, and the server.
- SSL on gaj2021.grabajab.com is supporting Transport Layer Security (TLS) version 1.0 and 1.1 which is commonly known as a vulnerable feature. These TLS versions should be disabled. TLS is a cryptographic protocol that secures communications security over a computer network.
- On gaj2021.grabajab.com no HTTP Strict Transport Security (HSTS) header is present on the web request response of https://gaj2021.grabajab.com. HSTS is a policy mechanism that helps protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. In this case, this is still possible since TLS 1.0 and TLS 1.1 are not disabled (as mentioned above).
- A high risk XSS (Cross-Site scripting), a type of security vulnerability typically found in web applications, was detected on the platform. XSS attacks enable malicious actors to inject client-side scripts into web pages viewed by other users. It may be used to bypass access controls.
- A missing X-Frame-Options Header which enables click-jacking attacks was detected. The X-Frame-Options HTTP response header can be used to avoid these attacks by ensuring that their content is not embedded into other sites.
We advise people in Lebanon not to use the platform for now.
We urge the Ministry of Public Health and IMPACT to explain the issue that took place on July 9. They must also run a strict security audit on GrabAJab and all platforms that collect personal data to ensure their safety and protect users’ privacy and data.


