When Israeli settlers and the police forces invaded Sheikh Jarrah, Palestinian activists and citizens took it to social media to expose the occupation’s daily violence against the families in the neighbourhood. Big Tech companies are silencing this Palestinian narrative and its supporters from all around the world through massive content takedown. They hid #Al_Aqsa hashtags, blocked and censored accounts and live streams, while shadowbanning Palestine-related content at large.
On May 10, 2021, the Israeli Army initiated a brutal airstrike operation, bombing vital infrastructures across the Gaza Strip. Internet infrastructure, local ISPs, and international media agencies were not spared.
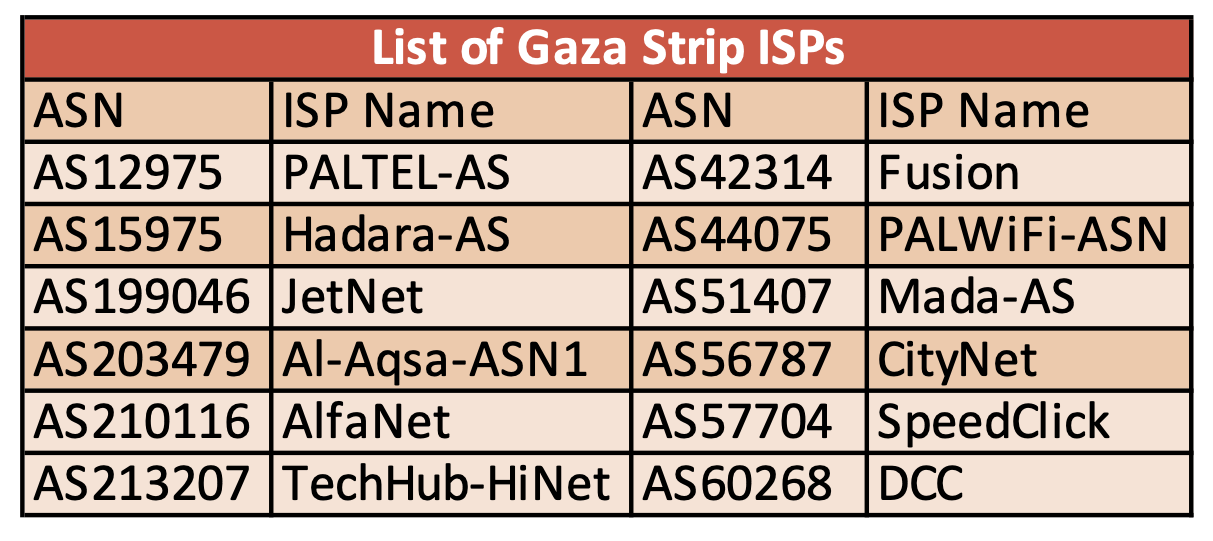
This report examines the internet disruption that affected internet supply across 12 local Internet Service Providers (ISPs) within the Gaza Strip during the Israeli raid of May 2021, before the “ceasefire” was declared (May 10-May 21).
This report relies on publicly available data and the statements published by the local ISPs. The technical outage data are retrieved from:
- Internet Outage Detection and Analysis – IODA, a real-time internet monitor
- RIPEstat, a large-scale information service and open data platform provided by RIPE NCC
- Cloudflare Radar, provides technical insight that occurs over Cloudflare’s network
Analysis of the available information lead to the conclusion that the Israeli Army deliberately targeted vital internet infrastructure, including high rise civilian towers, in what seems to be an attempted internet shutdown within the Gaza Strip as part of the information blackout on the violations occurring in the area.
Below is a technical note to understand the data examined in the report (in layman’s terms). These accessible definitions are provided to the more complicated technical terms and functions in the digital domain.
- BGP metric: Border Gateway Protocol (BGP) is the mechanism by which networks announce information on how to reach ranges of Internet Protocol (IP) addresses (prefixes). An outage could be detected if these networks stop announcing themselves to the internet.
- Active probing metric: Sending Ping requests to networks around the world. If several networks inside a country stop responding to pings, it could be interpreted as an outage.
- Dark Net metric: the number of unique IP addresses that are connected to a certain network. A drop in this metric means the IP addresses are offline.
Overall Traffic Change in the Palestinian Territories
Fetching data from Cloudflare’s Radar dashboard (April 27 – May 27, 2021), the Internet traffic in Palestinian Territories (West Bank and Gaza) has its daily normal fluctuation. According to Cloudflare, this metric, Change in Internet Traffic, shows the change in the amount of Internet traffic within the selected time range, based on data from its network.
On May 12, 2021, internet traffic drops and does not recover in the same way it had in the previous days. This trend in internet traffic continues, and around May 15 the traffic drops significantly to reach its lowest point on May 16 (x0.37 – based on the below graph). This shows that between May 12 and May 16, the Palestine Internet traffic had an unusual activity.
Examining Disruption Data per ISP
GazaNet (AS203905)
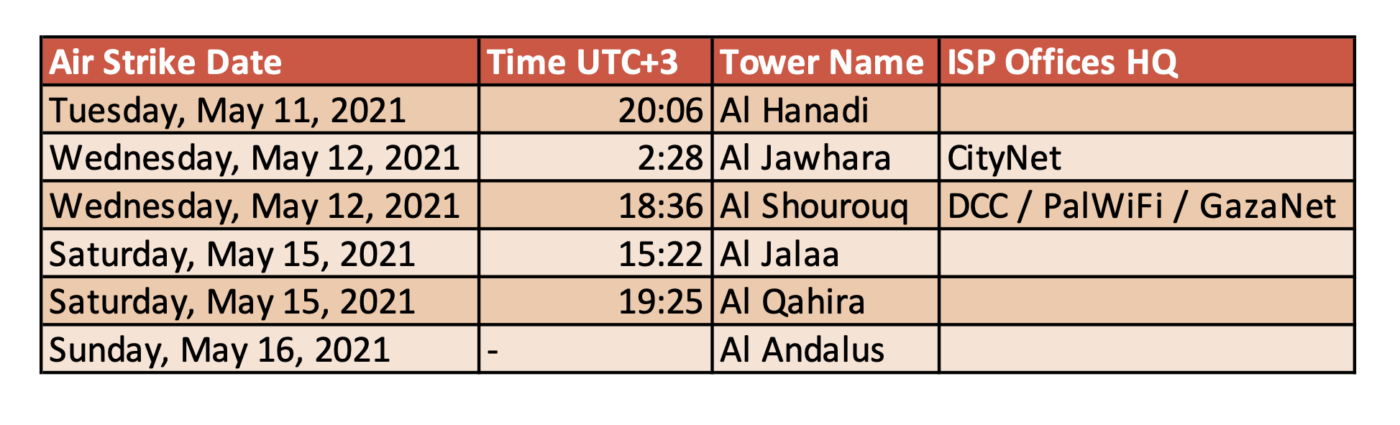
On May 12, 2021, GazaNet (AS203905) published on its Facebook page that the company’s equipment and servers have been destroyed by an Israeli airstrike on Al-Shourouq tower, which led to service disruption.
Note that GazaNet (AS203905) is a subsidiary of Digital Communication Company Palestine (AS60268).
SpeedClick Ltd (AS57704)
Based on IODA’s data, on May 12 around 07:00 (UTC+3) a sudden drop is noticed in SpeedClick’s (AS57704) active probing metric. The probing data kept fluctuating until it dropped further on May 14 at 00:40 (UTC+3). The service did not go back to normal until May 20 around 01:00 (UTC+3).
Within the same timeframe, both BGP (which is usually stable) and Dark Net metrics display a similar behaviour of sudden drop. Since all 3 metrics suffered a simultaneous drop, this implies that AS57704 suffered a mild outage, and the service began recovering around May 20.
Data from RIPEstat, confirms that a mild outage occurred. AS57704 announced 40 IPv4 prefixes on May 12, and then dropped to 35 on May 13. This means that 12.5% of the prefixes have gone offline.
SpeedClick (AS57704) was updating its users on the disruption events on a daily basis. On May 13, the company stated that it was not able to provide its services to 70% of its customers, and the supply to three governorates was disrupted (Deir al-Balah/central, Khan Younes, and Rafah) along with the southern lines of Gaza City.
Then on May 14, the internet service provider (ISP) stated that due to the ongoing bombing and airstrikes the company lost two main feeding lines, one of these lines being responsible for 52% of the company’s total internet capacity. And later on, the ISP said that the company is facing a total internet shutdown in the three southern governorates. In several other statements (1, 2), the ISP stated the severity of the damages done by airstrikes on its infrastructure (both Fiber and Wi-Fi supply).
Fusion (AS42314)
On May 12 and just after the leveling of Al-Jawahra tower that was hosting international broadcasts offices, Fusion (AS42314) stated on its Facebook page that one of its main servers had been severely damaged by the bombing of the tower, which led to service disruption.
Then on May 14, the ISP stated that further disruption to its service occurred due to the heavy bombardment of the Ansar Government Complex building in Gaza. Additionally, on May 18, the bombing of a house in the Beit Hanoun area led to the suspension of a transmission tower and disrupted the ISP’s service.
Furthermore, on May 19, Fusion (AS42314) clarified that some disruption in its services is due to a disruption in the supply from Palestinian Telecom Company (PALTEL AS12975).
TechHub-HiNet (AS213207)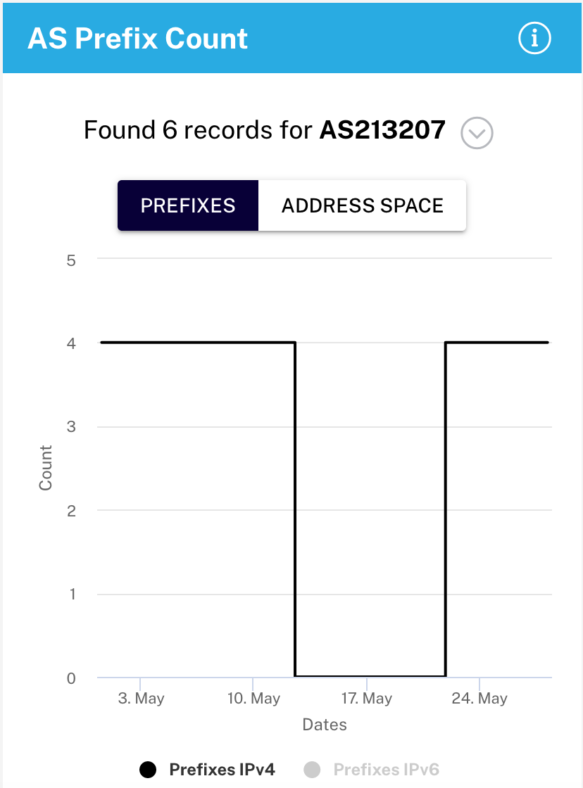
On May 12, TechHub-HiNet (AS213207) announced on its Facebook page that its upstream provider (SpeedClick Ltd – AS57704) had sustained severe damages at dawn. This statement matches the airstrike that hit Al-Jawhara tower (around 02:30 UTC+3).
Data from IODA indicates an outage on TechHub-HiNet (AS213207) network. The BGP routes suddenly dropped on May 12 at 11:55 (UTC+3) and went back to normal on May 22 at 05:00 AM (UTC+3). Data from RIPEstat concurs that all four IPv4 prefixes of AS213207 went offline. This proves that TechHub-HiNet suffered a total network shutdown for around 10 days.
Al-Aqsa-ASN1 (AS203479)
On May 12th, Al-Aqsa (AS203479) which is the service provider for Al-Aqsa University in Gaza witnessed a glitch in its BGP routing around 12:45 (UTC+3).
Quintiez Alfa General Trading Co. (AS210116)
Few minutes before the bombing of Al-Jalaa’ tower on May 15, AlfaNet (AS210116) notified its subscribers of a possible service disruption, as the main company’s office is located (Al-Watan tower) nearby the leveled tower. However, the ISP did not report any disruption later on.
Digital Communication Company (DCC) Palestine (AS60268)
On May 15, 2021, around 15:30 (UTC+3) the Israeli air force bombed Al-Jalaa’ tower in Gaza, which hosted several media offices like AP and Al Jazeera. Around the same time, DCC (AS60268) communicated on its Facebook page that there is an internet outage due to the leveling of the company’s main office at Al-Jalaa’ office.
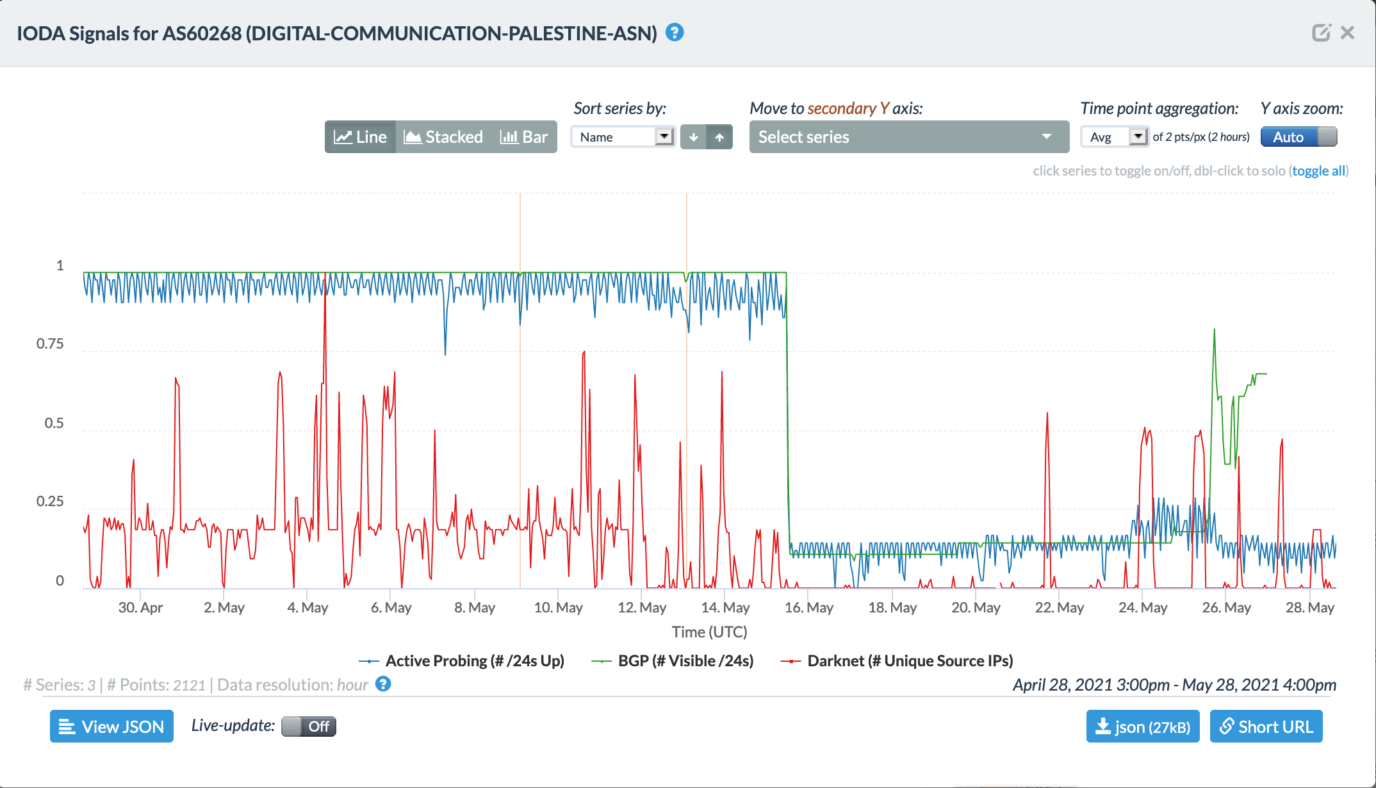
According to data from IODA, DCC’s (AS60268) three metrics (BGP, active probing, and dark net) suddenly dropped on May 15 at 15:40 (UTC+3). On a technical level, this means that the bombing directly relates to the internet outage on AS6o268.
When compared to data from RIPEstat, until approximately May 15 16:00 (UTC+3) AS60268 was recording32 IPv4 prefixes, and suddenly it dropped to 6, which means that 82% of its network went down. According to both IODA and RIPEstat DCC’s network started to recover on May 25.
CityNet (AS56787)
The sole upstream provider to CityNet (AS56787) is DCC Palestine (AS60268). Thus, in a similar fashion, three metrics (BGP, active probing, and dark net) data retrieved from IODA show that CityNet suffered a sudden total internet shutdown at 15:40 (UTC+3) due to the bombing of Al-Jalaa’ tower.
Data from RIPEstat, confirms the total outage of AS56787 as the 2 IPv4 prefixes suddenly went offline on May 15 at approximately 16:00 (UTC+3). Data from both IODA and RIPEstat concurred that the network did not recover back and is still offline (until the date of this report: May 28).
PALWiFi-ASN (AS44075)
DCC(AS60268) is also the sole provider to PALWiFi (AS44075), and the outage on this ISP is similar to both AS44075 and AS56787. The three metrics (BGP, active probing, and dark net) suddenly dropped to null on May 15 at 15:40 (UTC+3) which is interpreted as an internet outage.
However, RIPEstat’s data shows that on May 15, AS44075 only lost 50% of its IPv4 prefixes, and then it reached 75% by May 16. Both data sets (IODA & RIPEstat) show that PALWiFi-ASN started to recover on May 17 (75% back online) and went back fully online on May 18 (100%).
PALWiFi-ASN (AS44075) was able to recover faster than both DCC and CItyNet (AS44075 & AS56787), since it was able to get a new upstream provider which is SpeedClick Ltd (AS57704) starting May 17.
PALTEL-AS (AS12975)
In several public statements, PALTEL (AS12975) stated that its servers and internet infrastructure have been severely damaged due to the Israeli bombing.
Also, on May 19th, the company announced that its main Fiber Optics lines connecting both the central and southern governorates with Gaza City have been targeted. Additionally, another gateway that connects Gaza to the international gateway was destroyed. Thus, the ISP notified its users that a reduced service will be provided to southern governorates until it is able to repair the damages.
JetNet (AS199046)
Based on data from IODA, starting May 11 10:00 (UTC+3) a sudden drop in the active probing metric, which is interpreted as a disruption event. The probing data kept fluctuating until it went back to normal on May 16 at 00:00 (UTC+3).
Mada Al Arab-AS (AS51407) and Hadara-AS(AS15975)
No disruptions have been witnessed on the network of these ISPs.
Air Strikes Timetable and Interactive Map
Air Strikes Interactive Map
Conclusion
Based on both open source technical data and public statements published by companies SMEX can confirm that the below ISPs have suffered either mild, moderate internet disruption or total shutdown:
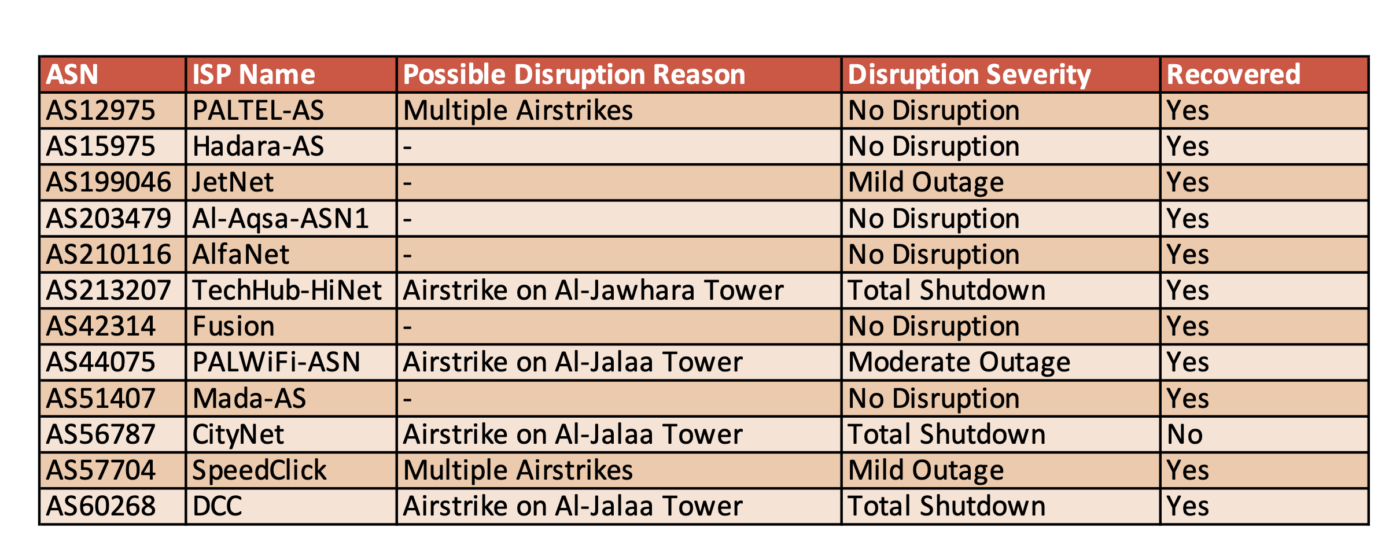
One third (4) of the 12 Gaza based ISPs SMEX examined, have suffered either total shutdown or moderate internet disruption. There is a direct casualty of these severe internet disruption which is the targeted bombing of two High Rise civilian towers in Gaza by the Israeli Army. The ISPs that were severely affected had infrastructure that were located in both Al-Jawahara and Al-Jalaa’ towers.
Also, other ISPs have been mildly affected by the “blind and random” raids on civilian compounds and buildings all around the Gaza Strip. Deducted from the public statements of the companies, the ISPs’ tech and maintenance teams were repairing (or replacing) all damaged infrastructure as soon as it was safe and rerouting the connection to reserve channels. Otherwise, for most days the civilians in Gaza Strip would have been totally cut off from the internet and the outer world.
It was also important to note that, the occupation’s government still hinder and suppress the development of the Palestinian internet landscape in general and Gaza Strip’s in specific, read more on this in 7amleh’s report.
The economic and financial cost of the damage incurred on the Gaza Strip’s internet infrastructure worth tens of millions of US dollars. EuroMed Monitor reported that one internet infrastructure (supply) company lost equipment worth 2 million USD when the Israeli Army warplanes targeted Al-Jawhara tower on May 12.
The recently approved UN Human Rights Council investigation probe needs to thoroughly investigate the targeting of internet infrastructure in Gaza Strip. The same UN body (UNHRC) has previously unequivocally condemned measures to intentionally prevent or disrupt access to dissemination of information online as a violation of international human rights law.



