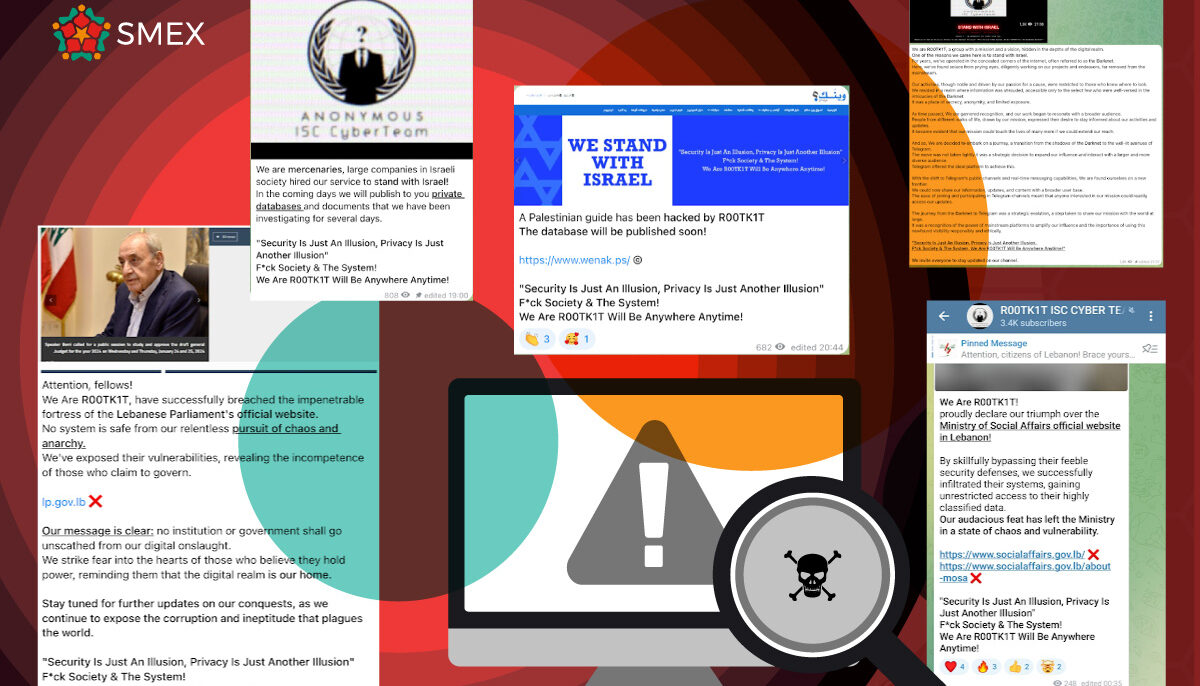
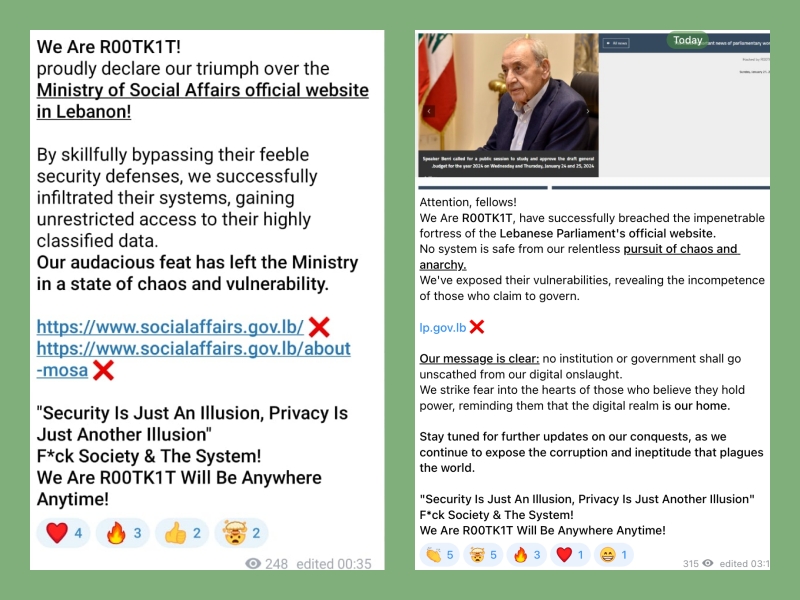
“We are ROOTK1T! Proudly declare our triumph over the Ministry of Social Affairs website in Lebanon,” announced a hacking group in a Telegram channel. The message celebrated “skillfully bypassing [the website’s] feeble security defenses” and “gaining unrestricted access to highly classified personal data.”
Mimicking the famous “We are Anonymous” slogan, R00TK1T, allegedly hired by Israeli mercenaries to “Stand with Israel,” warned users that over the coming days, they will be publicly publishing “private databases and documents.” No further information was provided on who was targeted or the type of data to be revealed.
On Monday, January 22, the Lebanese Social Affairs Ministry confirmed that their website was indeed hacked and that “work is underway to solve this problem.” It reassured citizens on X (previously Twitter) that the website “does not contain any personal information regarding beneficiaries of the Ministry’s programs.” Today, the Social Affairs Ministry’s website (socialaffairs.gov.lb) is back online.
The Lebanese Parliament’s official website was also compromised on Sunday, with another telegram message announcing: “We are R00TK1T, have successfully breached the impenetrable fortress of the Lebanese Parliament’s official website.” They claimed they hacked the voters’ database.
According to their Telegram channel, many Lebanese and Iranian websites have been targeted. They systematically attack websites and leak data, yet there’s no confirmation of a potential breach or the method of acquiring this information.
“Lebanese websites that got hacked have no data gathered on them. However, personal data, unfortunately, is being leaked or breached either by services and platforms from the different ministries or private companies,” says Mohamad Najem, Executive Director at SMEX.
While stating that they “stand with Israel,” this group has been active since the 1st of November 2023 under this name on Telegram, where they diffused a communication stating their purpose.
Not the first attack
On January 7, Beirut Rafic Hariri International Airport’s screens were hacked, displaying political messages instead of flight numbers and timings. The cyber breach also led to the temporary suspension of luggage belts. Lebanese officials are yet to announce their findings regarding the investigation of this incident.
Despite numerous cybersecurity incidents in recent years, the Lebanese government has not taken any substantial measures to protect its digital platforms against these hacks and breaches. In 2018, a spyware campaign dubbed “DNSpionage” targeted individuals and government websites in the UAE and Lebanon.
The attackers also targeted Lebanese private companies, including Middle East Airlines (MEA), Lebanon’s national flag-carrier airline. In 2019, a group named “Syrian Revolution Soldiers” (SRS) defaced the main page of the Rafic Hariri Airport’s website to display a political message.
Since October 7, residents of southern Lebanon have been receiving strange phone calls from strangers prying for personal information before Israeli strikes hit towns and villages. The callers’ numbers and accents are Lebanese.
Security officials believe these unusual calls are in fact from Israelis. Despite these facts, the Lebanese government did not take any public steps to protect Lebanon’s telecommunications networks nor investigate the incidents and how Israelis tapped into local networks. These most recent hacks targeting state websites could be part of a larger Israeli campaign to infiltrate Lebanese telecommunications networks, create a sense of public fear and panic, and scrape more data.
Recommendations for better cybersecurity on the country level
SMEX’s team have concluded some common weaknesses in Lebanese governmental IT infrastructure that we observed and potential solutions include:
1. Outdated Software and Systems:
- Weakness: Running outdated software or operating systems can expose vulnerabilities to be exploited by malicious actors, like what happened recently, defaced or code injection, which could conduct if the intentions are malicious will lead to a compromise of the system and sometimes leak of Personal Data. With the lack of a national Cyber Law and Cyber Security strategy, citizens’ information held by the government could be in danger.
- Solution: Regularly update and patch software, operating systems, and applications. Implement a system for continuous monitoring and prompt patching.
2. Insufficient Cybersecurity & Privacy Awareness:
- Weakness: Lack of awareness among employees about cybersecurity threats and best practices. Also lack of knowledge on how to handle personal data.
- Solution: Conduct regular cybersecurity training for employees. Emphasize the importance of strong passwords, recognizing phishing attempts, and reporting suspicious activities.
3. Inadequate Access Controls:
- Weakness: Poorly managed user access permissions may lead to unauthorized access.
- Solution: Implement a robust access control system, including the principle of least privilege. Regularly review and update user access rights. Use multi-factor authentication for sensitive systems.
4. Limited Incident Response Preparedness:
- Weakness: Insufficient preparation to respond effectively to security incidents.
- Solution: Develop and regularly update an incident response plan. Conduct regular drills and simulations to ensure a rapid and coordinated response to security incidents.
5. Poorly Secured Networks:
- Weakness: Insecure network configurations and inadequate network monitoring.
- Solution: Implement strong network security measures, including firewalls, intrusion detection/prevention systems, and encryption. Regularly audit and monitor network activities for anomalies.
6. Lack of Encryption:
- Weakness: Failure to encrypt sensitive data during transmission and storage.
- Solution: Implement encryption protocols for data in transit and data at rest. This includes using secure communication channels (e.g., HTTPS) and encrypting sensitive databases.
7. Supply Chain Vulnerabilities:
- Weakness: Inadequate vetting of third-party vendors and supply chain partners.
- Solution: Establish a rigorous vendor management program. Regularly assess and audit third-party security practices. Ensure that suppliers adhere to cybersecurity standards.
8. Insufficient Security Policies:
- Weakness: Lack of comprehensive cybersecurity policies and procedures.
- Solution: Develop and enforce clear cybersecurity policies covering areas such as data protection, acceptable use, and incident response. Regularly review and update policies to address evolving threats.
9. Inadequate Backups:
- Weakness: Failure to regularly back up critical data.
- Solution: Implement a robust backup and recovery strategy. Regularly test backup systems to ensure data can be restored in the event of a cyber incident.
10. Political and Geopolitical Factors:
- Weakness: Political instability and geopolitical factors may contribute to a challenging cybersecurity landscape.
- Solution: Establish a stable political environment that supports long-term cybersecurity initiatives. Collaborate with international partners for information sharing and assistance.
Addressing these weaknesses requires a comprehensive approach, involving technology, policy, and human factors. It’s important for the Lebanese government to collaborate with cybersecurity experts, engage in international cooperation, and invest in ongoing training and technology upgrades to enhance the resilience of its IT infrastructure.