With the ongoing war on Gaza since October 7, censorship, shadowbanning, and other new measures applied by tech companies, we are also noticing a rise in online attacks from harassment, hate speech, and fake news to phishing links and malware attacks. All these tactics serve one purpose: silencing the truth.
The digital Safety Helpdesk at SMEX has collected evidence to showcase how phishing links play a crucial role in the ongoing online war.
Phishing scams targeting page admins and account owners are not uncommon, but this trend grows during wars or global events. The following case occurred last July, seizing the AI trends, and it could fit with recent attacks.
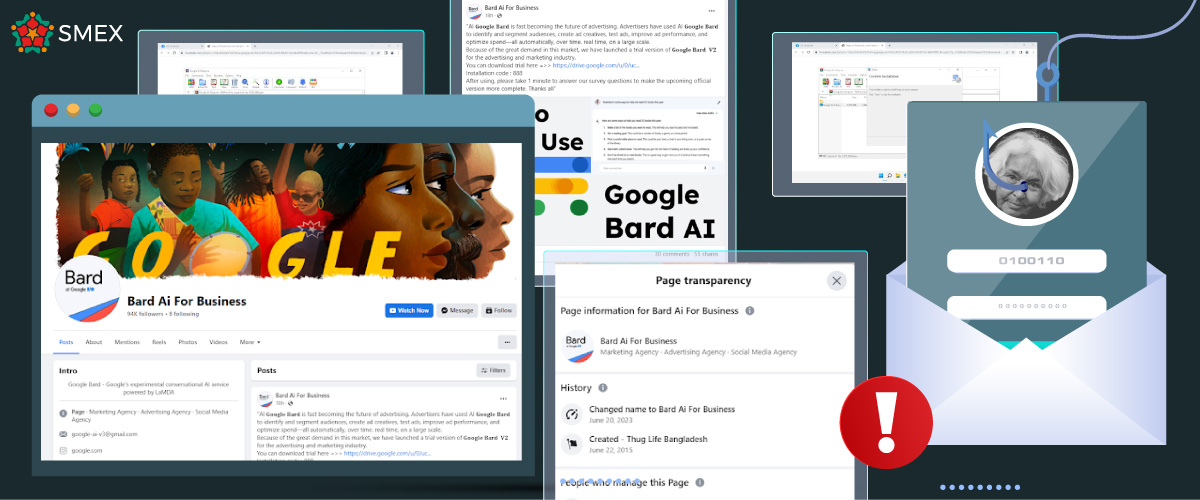
On July 7, the Helpdesk received a concerning case related to the Facebook page of a well-known Egyptian author and public figure, the late Nawal El-Saadawi, which has more than 400,000 followers. The page’s admin encountered a fake page that identified itself as the LaMDA-powered Marketing agency for Google’s Bard AI service. With around 94,000 followers, the page seemed credible enough that the admin clicked on one of the recent links posted on its profile.
The URL appeared authentic and even passed the “virustotal” test, a common program used to identify potential viruses. After clicking on the link, the admin was redirected to enter the account’s password, and as a result, lost all access to their page.
Further examination by SMEX’s Tech Team revealed that the page’s history was questionable. It was first launched in June 2015 as “Thug Life Bangladesh.” But in June 2023, it abruptly changed its name to “Bard Ai For Business,” which sparked concerns about a possible compromise. Additionally, there was a noticeable change in the type of content: instead of sharing memes, it promoted Bard AI. Most importantly, each post now contained an identical “phishing link.”
Additional investigation into the incident uncovered some technical information. When the user clicked on the “phishing link,” a fake “Google Translate” extension was downloaded and added to Chrome. Cookies which are small text files containing information about your website visit, such as your preferences and login information containing the user’s credentials that a website sends to your browser and stores on your computer or mobile device, were blocked from contacting the actual Facebook database, where credentials are usually stored, and sent through the fake Google Translate to be saved on a spreadsheet.
SMEX’s Helpdesk team was able to restore the users’ access to their hijacked accounts within hours, although Meta did not immediately remove the page despite our efforts. The page has now been removed.
As phishing attacks become more reliant on social engineering, allowing them to seamlessly pass as legitimate links to credible websites, emails, or event invites, internet users are advised to be cautious before clicking on any links online. The Digital Safety Helpdesk at SMEX advises vigilance while dealing with online links, especially those shared by unfamiliar or questionable sources.
- Before entering any important information, such as passwords, banking details, addresses, etc., be sure a page or an email is safe and secure.
- Use two-factor authentication (2FA) and set strong passwords with at least 16 characters on your platforms.
- Remember that credible companies typically include domain names in their contact email addresses.
- If you receive an email containing a link, you can see where it will redirect you by hovering the mouse over the link, which might reveal either an IP address or a web address, for example, in a little yellow or white box. This technique can help you detect a malicious link.
- Known entities, such as Google, Microsoft, or other large companies, always address the recipient by name when they send emails. If your name is not written correctly in the email, this is likely a phishing email.
- Phishing messages also try to inspire fear or excitement. For example, a phishing message may read, “If you don’t click this link, your email will be deactivated” or “free gifts.” If these messages are unexpected, they are likely phishing messages.
- Check the “From” and “To” fields of the email. If the email is not addressed to your email directly, something is “phishy.” If the email source seems legitimate, the sender could have still used hiding techniques in the email headers, as there are plenty of issues in mail servers.
- Legitimate entities use commonly known TLDs (Top-Level-Domains). Domains like .club, .tech, .win, etc., are likely fake pages. For example, Emirates Airlines will not send you a link with a .club link! They have a well-functioning .com domain name and care deeply about their SEO. They will not redirect you to a bizarre TLD. If you are not 100% certain about the real domain, you should search it on Google, Bing, DuckDuckGo, or another search engine.
- Complex domain names with many dashes, numbers, and dots are likely fake links. Therefore, the links could be part of a phishing campaign. For example, http://freeticket-xn--8973.smexclub[.]win is likely a phishing link.
- Words like “URGENT,” “GREETING,” or other words that denote immediate action are often used in phishing scams. For example, if you did nothing on the Apple website in the last 24 hours and are not expecting a message from the company, it is unlikely that it will send you an email with “URGENT” in the subject line. Be wary of messages with these words in the subject line.
- The vast majority of big companies have adopted HTTPS. If you don’t see a lock on your browser URL field, don’t proceed. In Firefox, the lock should be green, and in Google Chrome, you should click on the lock, and it should read encryption securely in green letters.
- The pages’ phishing links redirect you to request personal information. For example, these pages might request your name, phone, and/or email. Even if the web pages are not collecting passwords, collecting other personal information is a fundamental part of the reconnaissance phase of a staged hacking campaign. Never input your personal information on a website you do not trust.