— Article originally published on Global Voices Advocacy, by Zalfa Quino on the 28th July 2015 (Creative Commons Attribution 3.0) —

Red bird pilot by fORCEMATION via deviantart.com (CC BY 3.0)
Since the massive hack of the controversial Italian security and surveillance technology firm Hacking Team, journalists and human rights defenders in the Arab region have been carefully combing the 400GB of leaked data.
Hacking Team is best known for its “Remote Control System” which the leaks confirm has been used by oppressive regimes in Saudi Arabia, Bahrain, Sudan, UAE, Oman, Morocco and Egypt to surveil and intimidate political opponents, journalists, and human rights advocates.
Two weeks ago, WikiLeaks published more than 1 million searchable emails from the hack, which have shed light on the modus operandi of the firm’s team, their communication with clients, and their regular analysis of the political dynamics in the Middle East and elsewhere.
Gamers, beware
In a previous post, we explored leaked files confirming that the Lebanese Army purchased Hacking Team’s Galileo spy software, among other products. WikiLeaks’ searchable database indicates that Lebanon’s Interior Security Forces (ISF), General Security and the Cybercrime Bureau also contacted Hacking Team in an effort to purchase the software. A simple search for any of these terms in WikiLeaks database renders dozens of results.
Among emails exposed in the leak, the first signs of communication between ISF, its intelligence branch, and Hacking Team appear in 2014. These and all other communications between Lebanese officials and Hacking Team were mediated byPSEC & KAF, a private electrical and engineering services company in Lebanon.
Emails indicate [see PDF reproduction of email attachments]* that Hacking Team conducted a “proof of concept” demo on July 23-24, 2014 on the Interior Security Forces premises in Beirut. A rough translation of the report indicates that during the demo, ISF personnel were able to successfully infect target devices. With the help of Hacking Team staff, they created a technical “backdoor” in the devices (a virtual channel through which authorities can monitor a user’s activities) by exploiting a security flaw in the mobile phone game application Angry Birds:
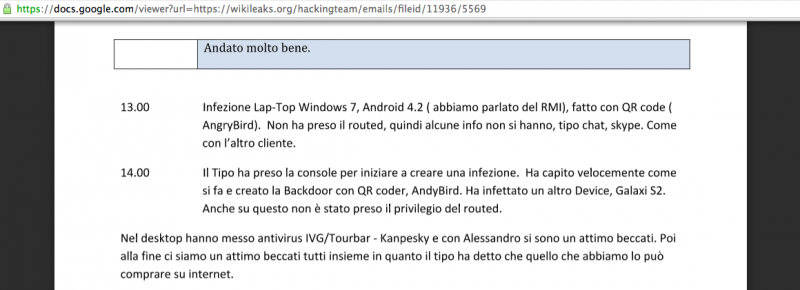
Along with the Lebanese Army and the Interior Security Forces, the Cybercrime Bureau established contact with Hacking Team on February 25, 2015. Their email read as follows:
Sirs,
This is cybercrime and IP Bureau-interior security forces-Lebanon.
Please note that we are a law enforcement agency in Lebanon,specialized in cybercrime investigations and we think that your software “GALLILEO-remote control system” could be helpful in our job.
Therefore,you are kindly requested to provide us with all the details about that software including the features,price,contact person and email address in case we need any support,and how this
software could be helpful in our criminal investigations.
Best Regards.
Cybercrime and IP bureau
Interior security forces
Further emails indicate that a demo for Galileo RCS took place in Beirut on March 30, 2015 in the offices of the Cybercrime Bureau. A reproduction of the report from the demo appears below.*
The report also indicates that the Cybercrime Bureau had contact with Gamma, another leading surveillance technology company and creator of FinFisher, a spyware product with capabilities similar to Hacking Team’s Remote Control System.
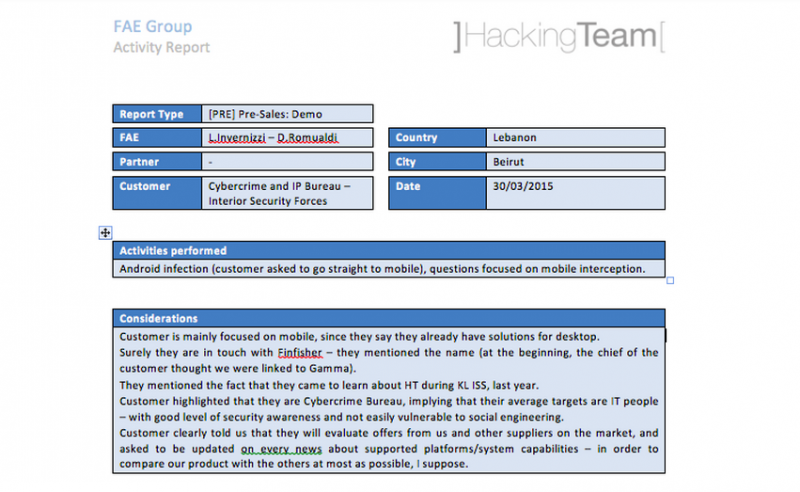
The demo focused mainly on mobile infection and interception. The demo and reports were followed by an offer revealing that the Cybercrime Bureau pursued a contract under which they targeted 50 individuals for a total of 450,000 Euros.
Targeting activists and bloggers
Several activists and bloggers who have been subject to repeated summons and investigations by the Lebanon’s “cyber watchdog”, the Cybercrime Bureau, now suspect that authorities used Hacking Team products to infect their devices and monitor their communications.
In a recent article on data privacy and digital surveillance in Lebanon, journalist Habib Battah described a tense local scenario in which citizens and various government agencies have widely varying interpretations of what constitutes lawful surveillance in Lebanon. Here, he summarizes a common approach taken by Lebanon’s Cybercrime Bureau in the course of investigations:
When summoned, the cyber crime bureau agents reportedly pressure bloggers to sign draconian documents vowing to refrain from mentioning the company or individuals they have criticized in the future. In some cases, bloggers have claimed that police agents tricked them into giving up information by sending malware to their computers, a practice [Major Suzan Hajj Hobeiche, head of the Cybercrime Bureau] seemed to endorse by claiming ‘ethical hacking’ used by law enforcement is sometimes needed to protect the greater good. Yet, increasingly that greater good seems to be defined by the interests of the wealthy and well-connected…many activists and lawyers worry that the bureau is unregulated and poses a threat to free speech.
How legal is Lebanon’s Cybercrime Bureau?
In its message to Hacking Team, the Cybercrime Bureau describes itself as a “law enforcement agency” within the Interior Security Forces. This is not entirely accurate. The Cybercrime Bureau was established under Memorandum 204/609 in 2006, but no decree was issued to amend the organizational structure of the Internal Security Forces, an amendment that is technically required for such a maneuver.
Many civil society advocates regard the bureau as an illegal entity. In a 2014 article for The Legal Agenda, lawyer Ghida Frangieh raised several questions regarding the vagueness of the bureau and its actual duties. Like Battah, she noted that over the last couple of years, multiple journalists, activists and bloggers were summoned by the bureau as part of an effort to have certain material removed or censored from the web.
Frangieh also pointed out that “despite the fact that the confidentiality of electronic communications is protected under Law 140/1999, this Bureau is equipped with the necessary technical capability to access private correspondence among Lebanese users.” In other words, the Cybercrime Bureau seems to be conducting surveillance outside the boundaries of local law — and using Hacking Team software to do it.
For more information about the Cybercrime Bureau and ongoing analysis of its actions follow @legalagenda, @smex and @maharat_Lebanon.
Bloggers and activists summoned to the Cybercrime Bureau can contact the Lebanese NGO March hotline for free legal advice and to be connected with competent lawyers and experts.
* Attachments to select emails mentioned in this story, and hosted on WikiLeaks, may contain malicious code. In order to avoid harm for our readers and our site, we took screen captures of the attachments using Google Docs Viewer and loaded them to our site as images. We advise anyone reviewing or opening attachments in emails from the Hacking Team leaks, whether on WikiLeaks or other sites, to proceed with caution.

